As each software development company, from time to time we pay some attention to SSL certificates. Such protection is a de-facto standard of modern web development as well as a very good practice which requires a constant expenditure of time and effort.
To use the SSL certificate we have to:
- Find a provider, which sells certificates
- Generate CSR
- Send it to the provider
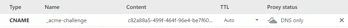
- Proof the domain ownership
- Get the certificate
- Optionally, transform it into the needed format, eg. PEM from to PKCS#12
- Install it to the web server.
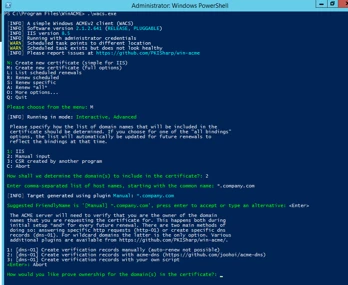
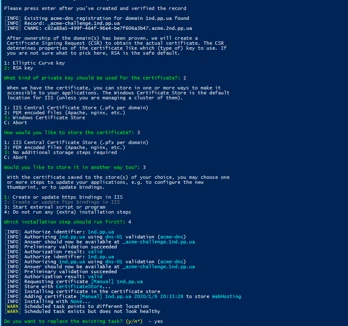
It seems to be easy when we have several projects at work. But what should we do if there are several dozen projects? And each consists of dev, staging, and production environments. In this case, we may try to automate this process. So, I want to describe the way to automate SSL purchase and share a solution that may reduce the time spent on this work. This article consists of my original research and experiments, as well as some instructions for easy implementation.
But be aware! As soon as UKAD provides mostly .NET development and related services, this article is Windows-oriented, so ACME client and whole procedures with it are described in the following way. With other operating systems it may differ a bit.
Introduction
We represent a company with URL company.tld
Project X is one of our projects, working on which I decided to reduce time spends. This project has four environments: dev, test, staging, and production. Dev and test are located on our side, while staging and production are located on the customer's side.
The thing is that Project X has a large number of modules that are developed as subdomains.
So, we have the following situation: